Check fraud causes hundreds of millions of dollars in financial damage to companies yearly. It is in their best interest to make sure that all their negotiable documents are as secure as possible against alteration and copying. Prescriptions are another item that is often copied or forged. The best approach to make sure a document is legitimate is through the use of multiple security features to keep unauthorized copies of the document being passed off as the original. Using paper that has alteration protection manufactured in provides another level of protection . A tried and true methodology most often used to provide a secure document is the strategy known as security feature stacking.
Stacking is when multiple security features are applied to a document to prevent unauthorized use. An example would be the use of a void pantograph, micro-printing, and watermarked paper. A warning band should be added to the document to alert the person receiving the document of the security features that have been used on the document.
Some Common Document Security Features
Warning Bands
Imagine having the worlds best alarm system, but you never turn it on. You can have all the security features available on a check and if no one knows about it, what good does that do? This is where a warning band comes into play. The warning band tells the receiver of the check to verify if the listed features are actually there on the document. If you are going to stack the features on a document, it does little good unless the receiver of the check or other document is aware of what safety features are integrated into the document. Usually the warning band is placed across the top of a document and it has a listing of the security features that you have chosen to incorporate into the document.

Colored Backgrounds
Many documents are produced with a background printed in a density of 10% or less in a color that contains no black or red. Typically a background produced in this manner will not copy if the document is scanned. This works best if a back and white printer is used to print the document.

Big Dot Little Dot and other Optical Screens:
The venerable big dot little dot system is still used to produce void pantographs. Other systems have been developed with varying success. All of these systems have a certain propensity to fail at some level. This reinforces the need for the stacking of security features. If one fails you have a back up.

Water Marked Paper:
One of the most secure methods of insuring that a document is the original is the use of water marked paper. A water mark can be a true (Fourdrinier), or an artificial water mark.
True Water Marks:
A true water mark (Fourdinier) is produced by a special roller as the paper is being manufactured. This mark becomes apparent when the paper is held up to light and is visible from the front or back of the document. A true watermark is difficult to reproduce. It cannot be be duplicated on either a scanner or a copier. The supply chain on most security paper is controlled by the manufacturer, keeping the product out of the hands of all but legitimate printers. A large buyer of water marked stock can have the mill produce a custom water mark for them.
Artificial Water Marks:
An artificial watermark can be produced by printing a pattern on the back of a document with transparent white or a coin reactive transparent white ink. To view the water mark image, the back of the document is usually tilted at a 45 degree angle to the light source in the room. Artificial watermarks can be words, logos or images. This allows for customization of the product while supplying a security feature at the same time. This water mark can only be viewed on the side on which they have been printed. This is usually the back of the form.
Coin Reactive Ink:
Coin reactive inks change color or become visible when scratched with a coin. This feature is often incorporated into transparent white ink used to produce artificial water marks. Coin reactive ink is a security feature that cannot be scanned or copied. It is often used on prescription pads to provide an easy verification of an original document at the pharmacy.
Colored and Ultraviolet Visible Fibers:
Some security papers are produced with visible fibers as part of the manufacturing process. The most commonly used fibers are red and blue colored. There is often the addition of fibers that are visible only under ultraviolet light. This is limited in effectiveness to those recipients that have an ultraviolet light source on hand. Colored fibers can be copied or scanned.
Chemical Reactive Paper:
Security papers often have the ability of react to common solvents that are being used to remove ink from a security document. Most often they turn a particular color in the area where the solvent was utilized. This gives a visual warning that the document has been altered.
Erasure Protection:
Erasure protection makes it more difficult to remove the ink that the check was signed or written with.
Toner Fast Paper:
When a document is printed, the ink seeps into the fibers of the paper and in essence becomes a part of the fiber. When a document is produced using toner, the toner lies on top of the fiber. Some of the toner adheres to the fibers but usually can be scraped off by a diligent individual. Toner fast paper has been manufactured so that toner more readily adheres to the document and cannot be easily removed.
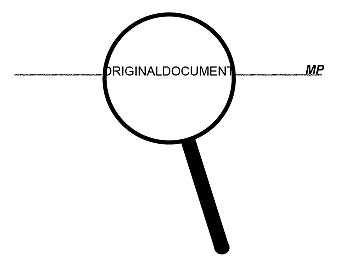
Micro-printing:
Type set at a size of 1 point or less. The type appears to be a line to the naked eye. When magnified the type can be clearly read. It is very difficult to copy or scan a document that will have readable micro-printing. When used on a document as a line it is usually indicated by MP at the end of the micro-print line. This feature of course only works if the recipient has a magnifier of sufficient strength to see the micro-print clearly.
Printed Backer:
A backer can be printed on the document with verbiage that notifies the receiver that this document is an original document. This is accomplished by using an ink that doesn't copy well, such as a light gray. Many documents also include micro-printing on the backer as another level of security against unauthorized duplication.

This list is by no means exhaustive, but it does provide an overview of different options for producing a secure document. Remember it is of little value to add security features if no one is aware that they are there. Use a warning band to get the message across that an effort has been made to protect this document. Let thieves look for easier pickings than your security feature stacked document.
For all your secure document needs call SEF, Inc., at 800-633-1228.
